Understand DKIM: Your Email Protection Shield
What is DKIM? It is an email authentication technique that helps protect against email spoofing and phishing. DKIM, which stands for DomainKeys Identified Mail, is a cryptographic signature that is added to outgoing emails. This signature allows receiving email servers to verify that the email is actually from the sender's domain and that it has not been tampered with in transit.
DKIM is important because it helps to protect email users from spam, phishing, and other malicious attacks. It also helps to improve email deliverability by ensuring that emails are not blocked by spam filters.
DKIM is a relatively new technology, but it is quickly becoming more widely adopted. Many major email providers, including Google, Microsoft, and Yahoo, now support DKIM. As DKIM adoption continues to grow, it will become increasingly difficult for spammers and phishers to spoof emails and launch successful attacks.
Here are some of the benefits of using DKIM:
- Protects against email spoofing and phishing
- Improves email deliverability
- Helps to build trust with email recipients
- Easy to implement and manage
If you are not already using DKIM, I encourage you to do so. It is a valuable tool that can help to protect your email users and improve your email deliverability.
DKIM
DKIM, short for DomainKeys Identified Mail, is an essential email authentication technique that safeguards against email spoofing and phishing. Its significance lies in protecting email users and enhancing email deliverability. Here are seven key aspects of DKIM:
- Cryptographic signature: Ensures message integrity and authenticity.
- Sender verification: Confirms the email originates from the claimed domain.
- Spam prevention: Helps identify and filter out unsolicited emails.
- Phishing protection: Safeguards against fraudulent emails attempting to steal sensitive information.
- Improved deliverability: Increases the likelihood of emails reaching their intended recipients.
- Trustworthy communication: Establishes trust between senders and recipients.
- Easy implementation: Simple to set up and manage for both senders and receivers.
These aspects collectively contribute to DKIM's effectiveness in securing email communication. By verifying the authenticity of emails and preventing spoofing, DKIM helps maintain the integrity of email communication and protect users from malicious attacks. Its adoption enhances email trust, promotes legitimate communication, and ensures emails reach their intended destinations.
Cryptographic signature
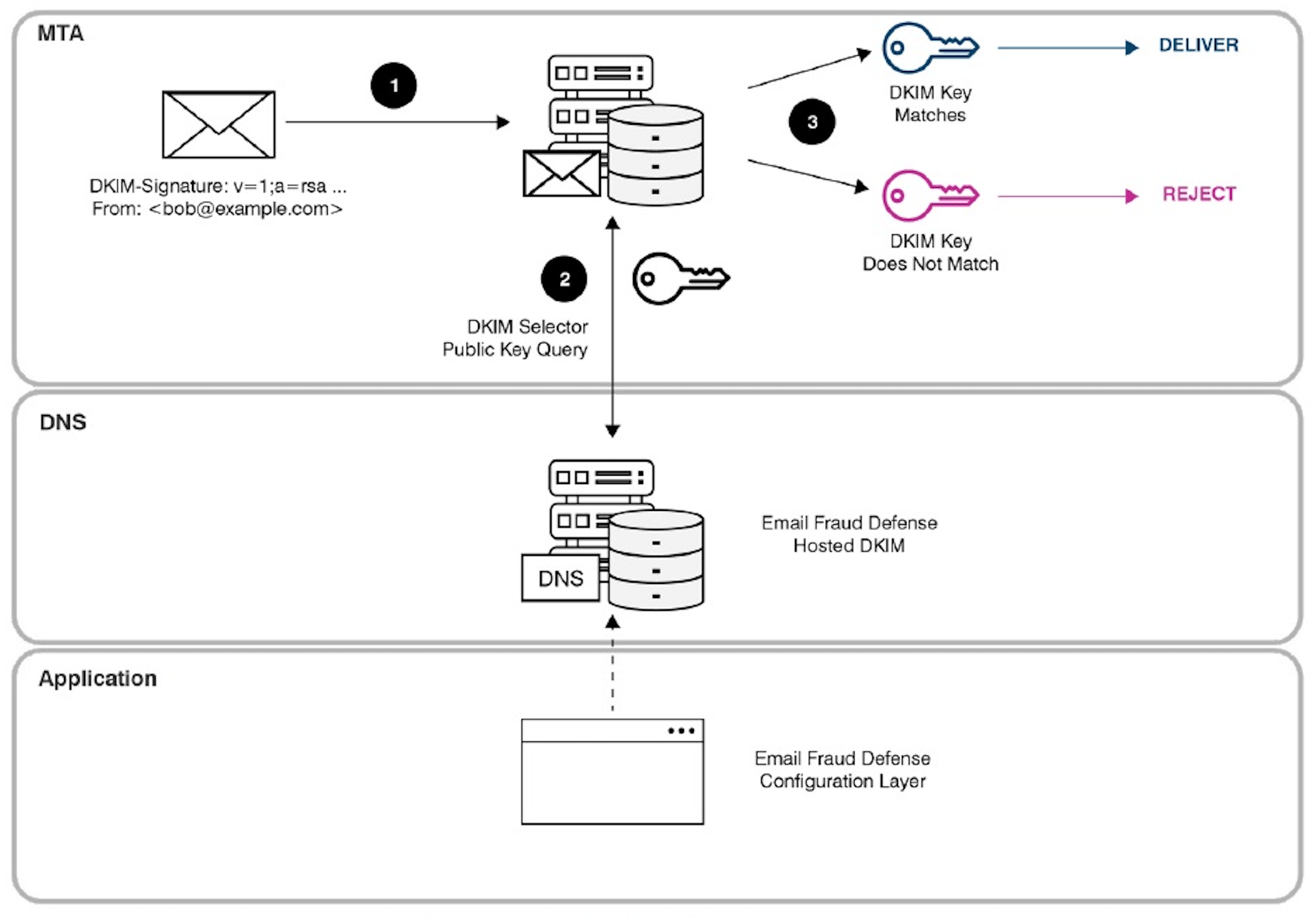
A cryptographic signature is a digital fingerprint that is used to verify the authenticity and integrity of a message. In the context of DKIM, a cryptographic signature is added to an email header. This signature is created using the sender's private key and can be verified using the sender's public key. If the signature is valid, it means that the email has not been tampered with in transit and that it was actually sent by the claimed sender.
Cryptographic signatures are an essential component of DKIM because they provide a way to verify the authenticity of emails. This is important for preventing email spoofing and phishing. Email spoofing is a technique that attackers use to send emails that appear to come from a legitimate sender. Phishing is a type of email fraud that attempts to trick recipients into revealing sensitive information, such as passwords or credit card numbers.
DKIM helps to prevent email spoofing and phishing by verifying the authenticity of emails. This helps to protect email users from malicious attacks and helps to ensure that emails are delivered to their intended recipients.
Sender verification
Sender verification is a critical component of DKIM. It allows receiving email servers to verify that the email is actually from the sender's domain and that it has not been spoofed. This is important for preventing email spoofing and phishing.
Email spoofing is a technique that attackers use to send emails that appear to come from a legitimate sender. This can be used to trick recipients into clicking on malicious links or opening attachments that contain malware. Phishing is a type of email fraud that attempts to trick recipients into revealing sensitive information, such as passwords or credit card numbers.
DKIM helps to prevent email spoofing and phishing by verifying the authenticity of emails. When an email is sent, the sender's email server adds a DKIM signature to the email header. This signature includes information about the sender's domain, the sender's public key, and a hash of the email body. The receiving email server can then use the sender's public key to verify the signature and ensure that the email has not been tampered with.
If the signature is valid, it means that the email is actually from the sender's domain and that it has not been spoofed. This helps to protect email users from malicious attacks and helps to ensure that emails are delivered to their intended recipients.
Sender verification is an essential component of DKIM. It helps to prevent email spoofing and phishing, and it helps to ensure that emails are delivered to their intended recipients.
Spam prevention
DKIM plays a vital role in spam prevention by assisting email servers in identifying and filtering out unsolicited emails. Spam emails, often referred to as junk mail, can be a nuisance and a security risk. DKIM helps mitigate this issue by providing a mechanism to verify the authenticity of emails and ensure they originate from legitimate sources.
When an email is sent, the sender's email server adds a DKIM signature to the email header. This signature includes information about the sender's domain, the sender's public key, and a hash of the email body. The receiving email server can then use the sender's public key to verify the signature and ensure that the email has not been tampered with.
If the signature is valid, it means that the email is actually from the sender's domain and that it has not been spoofed. This helps email servers identify and filter out spam emails, as spammers often use spoofed email addresses to trick recipients into opening malicious links or attachments.
DKIM's contribution to spam prevention is significant. By verifying the authenticity of emails, DKIM helps reduce the amount of spam that reaches users' inboxes. This not only improves the user experience but also helps protect users from malicious attacks and phishing scams.
Phishing protection
DKIM plays a crucial role in phishing protection by safeguarding users against fraudulent emails designed to steal sensitive information. Phishing scams often involve emails that appear to come from legitimate sources, such as banks or online retailers, but are actually attempts to trick recipients into revealing personal data like passwords or credit card numbers.
- Email Authentication: DKIM helps verify the authenticity of emails by adding a cryptographic signature to the email header. This signature includes information about the sender's domain and a hash of the email body. The receiving email server can then use the sender's public key to verify the signature and ensure that the email has not been tampered with.
- Protection against Spoofing: DKIM helps prevent phishing attacks by protecting against email spoofing. Spoofing is a technique used by attackers to send emails that appear to come from a legitimate sender, often using a forged email address. By verifying the sender's domain, DKIM ensures that the email is actually from the claimed sender and not a spoofed address.
- Enhanced Security: DKIM provides an additional layer of security to emails, making it more difficult for attackers to launch successful phishing attacks. By verifying the authenticity of emails, DKIM helps protect users from malicious links, attachments, and other phishing tactics.
- Increased User Trust: DKIM helps increase user trust in emails by ensuring that they are coming from legitimate sources. This can lead to improved email deliverability and reduced user skepticism towards emails, making it easier for businesses to communicate with their customers and partners.
In summary, DKIM's role in phishing protection is vital as it helps prevent fraudulent emails, protects against email spoofing, enhances overall security, and increases user trust in emails. By implementing DKIM, organizations and individuals can significantly reduce the risk of phishing attacks and protect sensitive information from falling into the wrong hands.
Improved deliverability
In the realm of email communication, deliverability plays a pivotal role in ensuring that emails successfully reach their intended recipients. DKIM, as an essential email authentication technique, holds significant sway over deliverability, positively influencing the likelihood of emails reaching their target audience.
The connection between DKIM and improved deliverability stems from its ability to verify the authenticity of emails and mitigate the risk of spam or phishing attempts. By digitally signing emails with a cryptographic signature, DKIM empowers receiving email servers to validate the sender's identity and the integrity of the email's content. This validation process helps distinguish legitimate emails from malicious ones, reducing the chances of emails being caught in spam filters or rejected altogether.
In a practical sense, implementing DKIM can significantly enhance email deliverability rates. Studies have shown that emails with valid DKIM signatures are more likely to land in recipients' inboxes, bypassing spam filters and ensuring timely delivery. This improved deliverability translates into increased visibility for legitimate emails, enabling effective communication and reducing the risk of important messages going unnoticed.
Moreover, DKIM's contribution to improved deliverability has a ripple effect on various aspects of email communication. Enhanced deliverability strengthens trust between senders and recipients, allowing for more reliable and efficient communication channels. It also bolsters the reputation of email domains, as recipients are more likely to engage with emails that are authenticated and free from malicious intent.
In summary, DKIM's role in improving deliverability is crucial for ensuring the effectiveness of email communication. By verifying email authenticity and combating spam, DKIM helps emails reach their intended recipients, fostering trust, and promoting seamless communication.
Trustworthy communication
In the digital age, where email communication is ubiquitous, establishing trust between senders and recipients is paramount. DKIM plays a pivotal role in fostering this trust by providing a robust mechanism to authenticate emails and ensure their integrity.
Trustworthy communication hinges on the ability of recipients to rely on the authenticity and legitimacy of emails they receive. DKIM achieves this by digitally signing emails with a cryptographic signature, which allows receiving email servers to verify the sender's identity and the integrity of the email's content. This validation process helps distinguish legitimate emails from malicious ones, reducing the risk of spoofing, phishing, and other fraudulent activities.
The practical significance of this trust-building mechanism is evident in various aspects of email communication. Firstly, it enhances the user experience by giving recipients confidence in the authenticity of emails they receive. This, in turn, increases the likelihood of emails being opened and acted upon, fostering more effective communication and stronger relationships between senders and recipients.
Moreover, DKIM contributes to the overall health and security of the email ecosystem. By reducing the prevalence of malicious emails, DKIM helps protect recipients from spam, phishing scams, and other cyber threats. This not only safeguards individual users but also promotes a more secure and reliable environment for businesses and organizations that rely on email for critical communications.
In summary, DKIM's role in establishing trustworthy communication is crucial for building trust, enhancing the user experience, and promoting a more secure email ecosystem. Its ability to authenticate emails and ensure their integrity lays the foundation for reliable and effective communication in the digital age.
Easy implementation
DKIM's simple implementation and straightforward management process contribute significantly to its widespread adoption and effectiveness. Its user-friendly design ensures that both senders and receivers can effortlessly integrate DKIM into their email infrastructure without encountering excessive complexities or technical barriers.
- Streamlined Setup for Senders:
For senders, implementing DKIM involves minimal effort. By generating a public/private key pair and publishing the public key in the DNS, senders can swiftly activate DKIM for their domain. This straightforward process allows senders to authenticate their emails without the need for extensive technical expertise or specialized software.
- Simplified Management for Receivers:
On the receiving end, DKIM verification is equally straightforward. Email servers can quickly validate DKIM signatures by retrieving the sender's public key from the DNS and comparing it to the signature in the email header. This automated process enables receivers to seamlessly authenticate emails without the need for manual intervention or complex configurations.
The ease of DKIM implementation and management offers several advantages. Firstly, it encourages widespread adoption, as organizations of all sizes and technical capabilities can readily deploy DKIM. This contributes to a more secure and reliable email ecosystem where malicious actors are less likely to succeed due to the prevalence of authenticated emails.
DKIM Frequently Asked Questions
This section addresses frequently asked questions (FAQs) about DKIM, providing concise and informative answers to common concerns and misconceptions.
Question 1: What is DKIM?
Answer: DKIM (DomainKeys Identified Mail) is an email authentication technique that helps protect against email spoofing and phishing. It works by adding a cryptographic signature to outgoing emails, allowing receiving email servers to verify that the email is actually from the sender's domain and that it has not been tampered with in transit.
Question 2: Why is DKIM important?
Answer: DKIM is important because it helps to protect email users from spam, phishing, and other malicious attacks. It also helps to improve email deliverability by ensuring that emails are not blocked by spam filters.
Question 3: How does DKIM work?
Answer: DKIM works by adding a cryptographic signature to the header of an email. This signature includes information about the sender's domain, the sender's public key, and a hash of the email body. The receiving email server can then use the sender's public key to verify the signature and ensure that the email has not been tampered with.
Question 4: How can I implement DKIM?
Answer: Implementing DKIM is relatively simple. You will need to generate a public/private key pair and publish the public key in your DNS records. Your email server will then automatically sign all outgoing emails with your DKIM signature.
Question 5: What are the benefits of using DKIM?
Answer: There are many benefits to using DKIM, including:
- Protects against email spoofing and phishing
- Improves email deliverability
- Helps to build trust with email recipients
- Easy to implement and manage
Question 6: Is DKIM required?
Answer: DKIM is not required, but it is highly recommended. It is a valuable tool that can help to protect your email users and improve your email deliverability.
Summary: DKIM is an essential email authentication technique that can help to protect against email spoofing and phishing. It is easy to implement and manage, and it offers a number of benefits, including improved email deliverability and increased trust with email recipients.
Transition: For more information on DKIM, please refer to the next article section.
DKIM
In conclusion, DKIM has emerged as a cornerstone of email security and deliverability, effectively combating spam, phishing, and other malicious activities. Its ability to authenticate emails and ensure their integrity has revolutionized email communication, enhancing trust and reliability.
As the digital landscape continues to evolve, DKIM will undoubtedly play an increasingly critical role in protecting email users and safeguarding the integrity of email communication. Its widespread adoption and continued development will contribute to a more secure and efficient email ecosystem for all.
Optimize Your Spark Performance With Enhanced Executor Instances
Discover A Random Number Generator: Select Your Fortune Now
Discover The Significance Of Requesting Signed Artwork: Unveiling Authenticity And Enhancing Value