A Guide To Creating Private SSH Sourcetree: Securely Store And Collaborate On Code
How to Create a Private SSH Key for Sourcetree
A private SSH key is a secure way to connect to a remote server. It is more secure than using a password, as it does not require you to enter your password each time you connect. To create a private SSH key for Sourcetree, follow these steps:
- Open Sourcetree and go to the Accounts tab.
- Click on the "SSH Keys" tab.
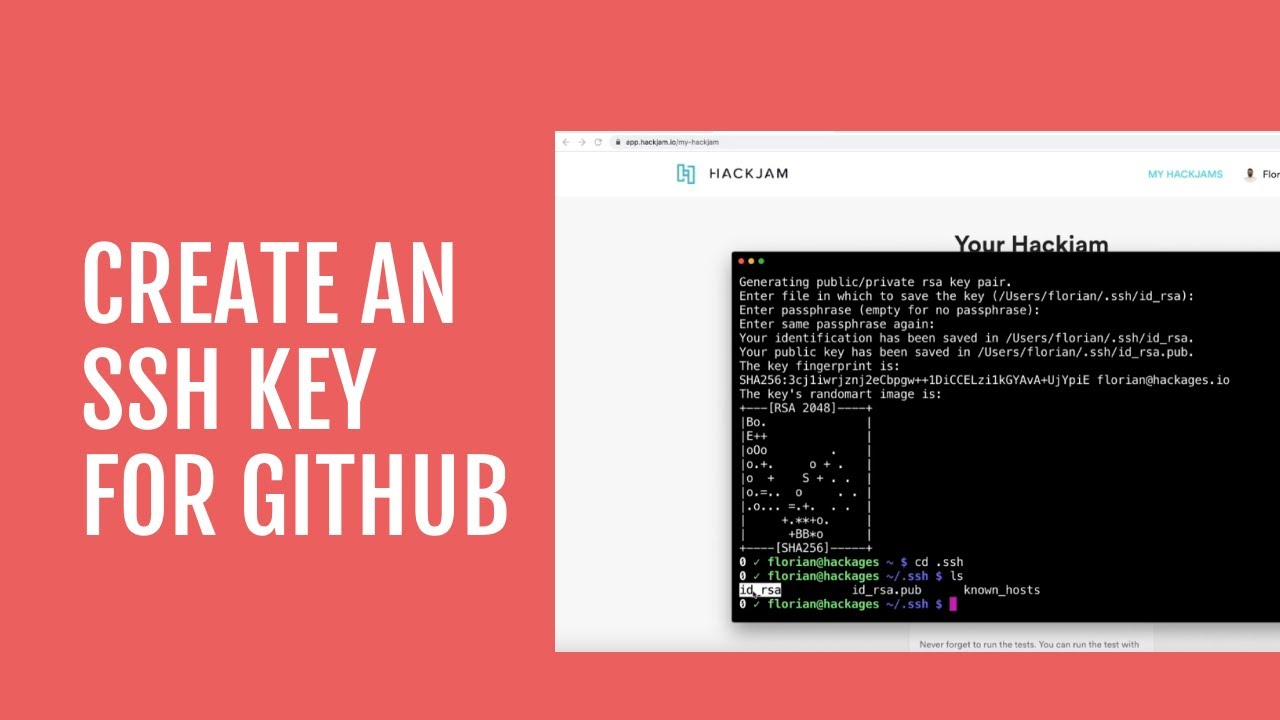
- Click on the "Generate" button.
- Enter a name for your key and click on the "Generate" button.
- Your private SSH key will be saved to your computer. You can now use this key to connect to remote servers.
Using a private SSH key has several benefits, including:
- It is more secure than using a password.
- It is more convenient, as you do not have to enter your password each time you connect.
If you are using Sourcetree to connect to a remote server, it is recommended that you create a private SSH key. This will help to keep your connection secure and convenient.
How to Create a Private SSH Key for Sourcetree
Creating a private SSH key for Sourcetree is an essential step for securely connecting to remote servers. This guide will explore six key aspects of this process, providing a comprehensive understanding of the topic.
- Security: Private SSH keys offer enhanced security compared to passwords, protecting against unauthorized access.
- Convenience: Eliminates the need for repeated password entry, streamlining the connection process.
- Generation: Sourcetree provides a user-friendly interface for generating private SSH keys.
- Storage: Private SSH keys are securely stored on the user's computer, ensuring their safety.
- Usage: Private SSH keys can be used to connect to remote servers, facilitating code management and collaboration.
- Compatibility: Sourcetree supports the use of private SSH keys, ensuring seamless integration with other tools.
In summary, creating a private SSH key for Sourcetree is crucial for establishing secure and convenient connections to remote servers. By leveraging the key aspects discussed above, users can effectively protect their data, streamline their workflow, and enhance their overall development experience.
Security
In the context of creating a private SSH key for Sourcetree, security is of paramount importance. Private SSH keys provide a significantly higher level of security compared to passwords, effectively protecting against unauthorized access to remote servers. This enhanced security stems from the cryptographic principles underlying SSH keys, which make it computationally infeasible for unauthorized individuals to decipher the key and gain access to the server.
The importance of security in this context cannot be overstated. Remote servers often contain sensitive data, including source code, confidential information, and user credentials. Using a password for authentication poses a significant risk, as passwords can be easily compromised through various methods such as brute force attacks, phishing, or social engineering. In contrast, private SSH keys offer a robust and reliable form of authentication, ensuring that only authorized users with the corresponding private key can access the server.
To illustrate the practical significance of this enhanced security, consider a scenario where an unauthorized individual gains access to a remote server due to a compromised password. This could lead to catastrophic consequences, including data theft, system disruption, or even financial loss. By utilizing a private SSH key, organizations and individuals can drastically reduce the risk of such security breaches, safeguarding their sensitive data and maintaining the integrity of their systems.
Convenience
In the context of creating a private SSH key for Sourcetree, convenience plays a significant role in enhancing the user experience and streamlining the connection process to remote servers.
- Elimination of Repetitive Password Entry: Private SSH keys eliminate the need for repeatedly entering passwords when connecting to remote servers. This provides a seamless and efficient workflow, especially for users who frequently connect to multiple servers throughout the day.
- Simplified Authentication: By utilizing a private SSH key, users only need to enter a passphrase during the initial setup. This simplifies the authentication process, reducing the risk of errors and saving valuable time.
- Automated Login: Private SSH keys enable automated login to remote servers, further enhancing convenience. Once configured, users can establish secure connections without any manual intervention, streamlining their development and collaboration processes.
The convenience offered by private SSH keys is particularly advantageous in agile development environments, where developers frequently interact with remote repositories and servers. By eliminating the need for password entry and automating login, private SSH keys contribute to increased productivity and efficiency, enabling developers to focus on their core tasks without unnecessary interruptions.
Generation
The ability to generate private SSH keys through a user-friendly interface is a critical component of the overall process of creating a private SSH key for Sourcetree. This feature plays a pivotal role in simplifying the key generation process, making it accessible to users of all levels.
The user-friendly interface provided by Sourcetree eliminates the need for complex command-line interactions or manual configuration, which can be daunting for beginners. The graphical interface guides users through each step of the key generation process, ensuring that the keys are created securely and correctly.
The importance of this user-friendly interface cannot be overstated. Generating private SSH keys is an essential step for establishing secure connections to remote servers. By providing a straightforward and intuitive interface, Sourcetree empowers users to create strong SSH keys without the need for specialized technical knowledge.
Storage
In the context of creating a private SSH key for Sourcetree, the secure storage of private SSH keys is paramount, as it ensures the integrity and confidentiality of the key.
- Encryption: Private SSH keys are encrypted with a passphrase, providing an additional layer of security. Even if the key file is compromised, the encrypted key cannot be used without the passphrase.
- Local Storage: Private SSH keys are stored on the user's local computer, giving the user full control over the key and reducing the risk of remote access or theft.
- Key Management: Sourcetree provides secure key management features, allowing users to easily add, remove, and manage multiple SSH keys.
- Security Best Practices: Proper storage practices, such as using strong passphrases and avoiding storing the key on publicly accessible locations, enhance the overall security of the private SSH key.
By securely storing private SSH keys on the user's computer, Sourcetree ensures the safety and integrity of the key, mitigating the risk of unauthorized access and protecting the user's remote connections.
Usage
The usage of private SSH keys for connecting to remote servers is a crucial component of "how to create private ssh sourcetree." SSH (Secure Shell) is a network protocol that provides secure remote access to servers. By utilizing private SSH keys, users can establish secure connections to remote servers for various purposes, including code management and collaboration.
In the context of code management, private SSH keys enable developers to securely access remote repositories hosted on platforms such as GitHub or Bitbucket. This allows them to clone, pull, push, and manage code changes efficiently. Moreover, SSH keys facilitate seamless collaboration among team members, allowing them to share and work on codebases remotely without the need to share passwords.
The practical significance of understanding this connection lies in the enhanced security and convenience it offers. Private SSH keys provide a more secure alternative to passwords, reducing the risk of unauthorized access to remote servers and protecting sensitive data. Additionally, the elimination of password entry streamlines the connection process, improving productivity and collaboration.
In summary, the usage of private SSH keys for connecting to remote servers is an integral aspect of "how to create private ssh sourcetree." It enables secure and efficient code management and collaboration, highlighting the importance of understanding this connection for effective remote development and teamwork.
Compatibility
The compatibility of Sourcetree with private SSH keys is a crucial aspect of "how to create private ssh sourcetree." This compatibility enables seamless integration with other tools and services, enhancing the overall development workflow and productivity.
Private SSH keys provide a secure and efficient way to connect to remote servers and repositories. By integrating with private SSH keys, Sourcetree allows developers to leverage this security and efficiency within their preferred development environment. This integration eliminates the need for additional plugins or tools, streamlining the development process and reducing potential compatibility issues.
The practical significance of this compatibility lies in its ability to facilitate seamless code management and collaboration. Developers can securely access and manage remote repositories using their private SSH keys, enabling them to clone, push, pull, and merge code changes securely and efficiently. Additionally, this integration allows developers to utilize other tools and services that rely on SSH authentication, such as issue trackers, CI/CD pipelines, and deployment tools.
In summary, the compatibility of Sourcetree with private SSH keys is an essential component of "how to create private ssh sourcetree." It provides secure and seamless integration with other tools and services, enhancing the overall development workflow and productivity. Understanding this compatibility is crucial for developers seeking to leverage the full capabilities of Sourcetree and establish efficient remote development and collaboration practices.
Frequently Asked Questions about Creating Private SSH Keys for Sourcetree
This section addresses common concerns and misconceptions surrounding the creation and usage of private SSH keys for Sourcetree, providing concise and informative answers.
Question 1: Why is it important to use a private SSH key for Sourcetree?
Using a private SSH key offers enhanced security compared to passwords, protecting against unauthorized access to remote servers and safeguarding sensitive data during code management and collaboration.
Question 2: How do I generate a private SSH key for Sourcetree?
Sourcetree provides a user-friendly interface for generating private SSH keys. Navigate to the SSH Keys tab within the Accounts section, click "Generate," enter a name for your key, and click "Generate" again. Your private SSH key will be securely stored on your computer.
Question 3: How do I use my private SSH key to connect to a remote server?
Once generated, you can use your private SSH key to establish a secure connection to a remote server. Configure your SSH client (e.g., PuTTY, OpenSSH) to use the private SSH key, enter the server's hostname or IP address, and connect.
Question 4: How do I manage multiple private SSH keys in Sourcetree?
Sourcetree allows you to manage multiple SSH keys for different servers or accounts. Go to the SSH Keys tab, click "Add," and provide the necessary details. You can switch between keys easily when connecting to different servers.
Question 5: Is it safe to store my private SSH key on my computer?
Yes, it is generally safe to store your private SSH key on your computer, provided you take appropriate security measures. Ensure your computer has strong antivirus protection, use a passphrase to encrypt the key, and avoid storing the key in publicly accessible locations.
Question 6: What should I do if I lose my private SSH key?
If you lose your private SSH key, you will need to generate a new one. Additionally, you may need to contact the server administrator to revoke access using the old key. Remember to update your SSH configuration to use the new key.
Understanding these FAQs will help you effectively create, manage, and use private SSH keys for Sourcetree, enhancing the security and efficiency of your remote development workflow.
Return to main article
Conclusion
Creating a private SSH key for Sourcetree is a fundamental step for establishing secure and efficient remote development workflows. By understanding the key aspects explored in this article, developers can effectively utilize private SSH keys to protect their sensitive data, streamline their connection processes, and enhance their overall development experience.
The adoption of private SSH keys is becoming increasingly crucial in today's collaborative development environments, where secure access to remote servers and repositories is paramount. By embracing the best practices outlined in this article, developers can proactively safeguard their projects, foster seamless collaboration, and drive innovation forward.
Master Ruby Development In Visual Studio Code: The Ultimate Guide
Is Brutus: The Pivotal Protagonist Of Shakespeare's Masterpiece?
How To Do Git Merge: A Step-by-Step Guide
![How to SSH Through Bastion With Key [Tutorial]](https://i2.wp.com/discover.strongdm.com/hs-fs/hubfs/Imported_Blog_Media/605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key-2.jpg?width=1950&height=1095&name=605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key-2.jpg)